IPv6 Sandbox
Details
- Location: KringleCon/Talks Lobby
- Elf: Jewel Loggins
Elf's Objective Message
Well hello! I'm Jewel Loggins.
I have to say though, I'm a bit distressed. The con next door? Oh sure, I’m concerned about that too, but I was talking about the issues I’m having with IPv6. I mean, I know it's an old protocol now, but I've just never checked it out. So now I'm trying to do simple things like Nmap and cURL using IPv6, and I can't quite get them working! Would you mind taking a look for me on this terminal? I think there's a Github Gist that covers tool usage with IPv6 targets. The tricky parts are knowing when to use [] around IPv6 addresses and where to specify the source interface. I’ve got a deal for you. If you show me how to solve this terminal, I’ll provide you with some nice tips about a topic I’ve been researching a lot lately – Ducky Scripts! They can be really interesting and fun!
This terminal is located in the Talks Lobby at KringoleCon. Solving this terminal challenge provides additional hints for objective 5. To view the hints for this terminal challenge use the menu on the left.
When you open the terminal you are greeted with the following window:
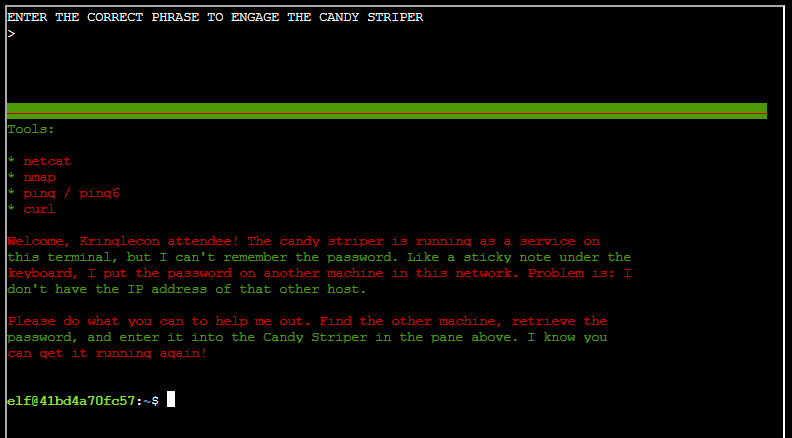
To solve this challenge you need to enter the correct phrase to engage the candy striper.
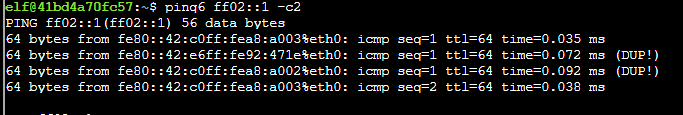
To find link local addresses for systems in your network segment, use the command 'ping6 ff02::1 -c2'.
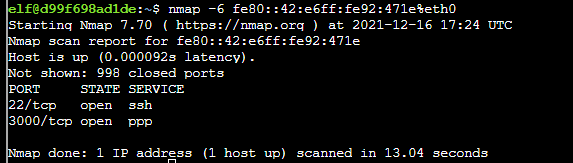
To find open ports on these two hosts use the commands nmap -6 fe80::42:c0ff:fea8:a003%eth0 and nmap -6 fe80::42:e6ff:fe92:471e%eth0.
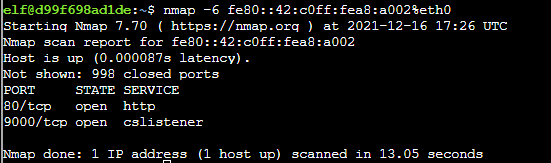
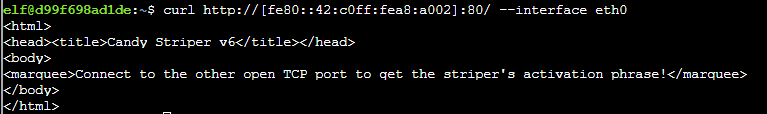
Use curl to connect to port 80 on host fe80::42:c0ff:fea8:a002 using the command curl http://[fe80::42:c0ff:fea8:a002]:80/ --interface eth0.
Follow the instructions and connect to port 9000 using the command curl http://[fe80::42:c0ff:fea8:a002]:9000/ --interface eth0.
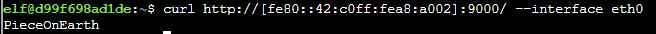
Type the response returned from the server in the top of the terminal to solve this challenge.
Answer
PieceOnEarth