Hints¶
This page will provide various hints that were provided by the game for objectives challenges.
Objective Hints¶
Objectives
No hints.
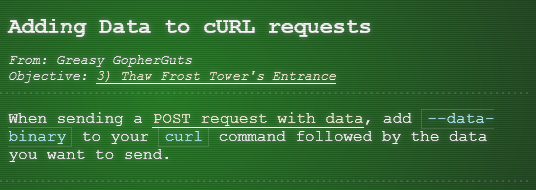
Hint 1 Link
- POST request with data: Link
Hint 2 Link
- cURL: Link
Greasy GopherGuts's Hint
You really did it?
Well, OK then. Here's what I know about the wifi here. Scanning for Wi-Fi networks with iwlist will be location-dependent. You may need to move around the North Pole and keep scanning to identify a Wi-Fi network. Wireless in Linux is supported by many tools, but iwlist and iwconfig are commonly used at the command line. The curl utility can make HTTP requests at the command line! By default, curl makes an HTTP GET request. You can add --request POST as a command line argument to make an HTTP POST request. When sending HTTP POST, add --data-binary followed by the data you want to send as the POST body.
Hint 1 Link
- parameter tampering: Link
Noel Boetie's Hint
Wow - amazing score! Great work!
So hey, those slot machines. It seems that in his haste, Jack bought some terrible hardware. It seems they're susceptible to parameter tampering parameter tampering. You can modify web request parameters with an intercepting proxy or tools built into Firefox.
Hint 1 Link
- MITRE ATT&CK(TM) tactic T1098.004: Link
Hint 2 Link
- Mallard: Link
Hint 3 Links
- duck encoder: Link
Hint 4 Links
- Ducky Script: Link
Jewel Loggins's Hint
Great work! It seems simpler now that I've seen it once. Thanks for showing me!
Prof. Petabyte warned us about random USB devices. They might be malicious keystroke injectors!
A troll could program a keystroke injector to deliver malicious keystrokes when it is plugged in. Ducky Script is a language used to specify those keystrokes. What commands would a troll try to run on our workstations? I heard that SSH keys can be used as backdoors. Maybe that's useful?
Chimney Scissorsticks's Hint
Great work! It seems simpler now that I've seen it once. Thanks for showing me!
Prof. Petabyte warned us about random USB devices. They might be malicious keystroke injectors!
A troll could program a keystroke injector to deliver malicious keystrokes when it is plugged in. Ducky Script is a language used to specify those keystrokes. What commands would a troll try to run on our workstations? I heard that SSH keys can be used as backdoors. Maybe that's useful?

Hint 1 Link

Hint 2 Link
- Hash Extension Attacks: Link

Ruby Cyster's Hint
Oh man - what is this all about? Great work though.
So first things first, you should definitely take a look at the firmware. With that in-hand, you can pick it apart and see what's there. Did you know that if you append multiple files of that type, the last one is processed? Have you heard of Hash Extension Attacks? If something isn't working, be sure to check the output! The error messages are very verbose. Everything else accomplished, you just might be able to get shell access to that dusty old thing!

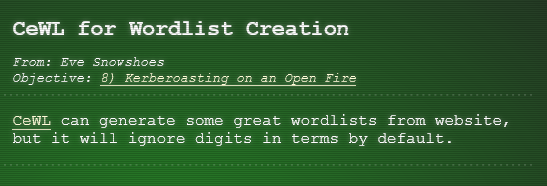
Hint 3 Links
- CeWL: Link

Hint 4 Links
- OneRuleToRuleThemAll.rule: Link
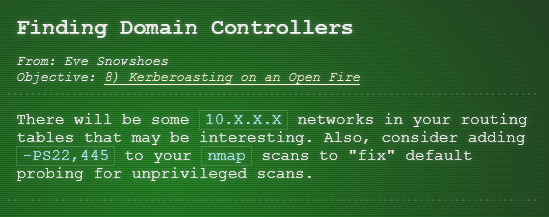

Hint 6 Links
- Kerberoasting: Link
Eve Snowshoes's Hint
Fantastic! Thanks for the help!
Hey, would you like to know more about Kerberoasting and Active Directory permissions abuse?
There's a great talk by Chris Davis on this exact subject!
There are also plenty of resources available to learn more about Kerberoasting specifically. If you have any trouble finding the domain controller on the 10.X.X.X network, remember that, when not running as root, nmap default probing relies on connecting to TCP 80 and 443. Got a hash that won't crack with your wordlist? OneRuleToRuleThemAll.rule is a great way to grow your keyspace. Where'd you get your wordlist? CeWL might generate a great wordlist from the ElfU website, but it will ignore digits in terms by default. So, apropos of nothing, have you ever known system administrators who store credentials in scripts? I know, I know, you understand the folly and would never do it! The easy way to investigate Active Directory misconfigurations (for Blue and Red alike!) is with Bloodhound, but there are native methods as well. Oh, and one last thing: once you've granted permissions to your user, it might take up to five minutes for it to propogate throughout the domain.
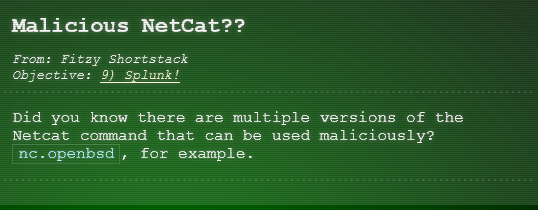

Fitzy Shortstack's Hint
Thanks - you figured it out!
Let me tell you what I know about Splunk.
Did you know Splunk recently added support for new data sources including Sysmon for Linux and GitHub Audit Log data?
Between GitHub audit log and webhook event recording, you can monitor all activity in a repository, including common git commands such as git add, git status, and git commit. You can also see cloned GitHub projects. There's a lot of interesting stuff out there. Did you know there are repositories of code that are Darn Vulnerable? Sysmon provides a lot of valuable data, but sometimes correlation across data types is still necessary. Sysmon network events don't reveal the process parent ID for example. Fortunately, we can pivot with a query to investigate process creation events once you get a process ID. Sometimes Sysmon data collection is awkward. Pipelining multiple commands generates multiple Sysmon events, for example. Did you know there are multiple versions of the Netcat command that can be used maliciously? nc.openbsd, for example.
Hint 1 Link
- AWS Documentation for IMDS: Link
Noxious O. D'or's Hint
Phew! That is something extra! Oh, and you solved the challenge too? Great!
Cloud assets are interesting targets for attackers. Did you know they automatically get IMDS access?
I'm very concerned about the combination of SSRF and IMDS access. Did you know it's possible to harvest cloud keys through SSRF and IMDS attacks? Dr. Petabyte told us, "anytime you see URL as an input, test for SSRF." With an SSRF attack, we can make the server request a URL. This can reveal valuable data! The AWS documentation for IMDS is interesting reading.
Hint 1 Link
- display filters: Link
Hint 1 Link
- RFC3514: Link
Noxious O. D'or's Hint
Great! Thanks so much for your help!
I'm sure I can put those skills I just learned from you to good use.
Are you familiar with RFC3514?
Wireshark uses a different name for the Evil Bit: ip.flags.rb. HTTP responses are often gzip compressed. Fortunately, Wireshark decompresses them for us automatically. You can search for strings in Wireshark fields using display filters with the contains keyword.
Ribb Bonbowford's Hint
Gosh, with skills like that, I'll bet you could help figure out what's really going on next door...
And, as I promised, let me tell you what I know about SQL injection.
I hear that having source code for vulnerability discovery dramatically changes the vulnerability discovery process.
I imagine it changes how you approach an assessment too. When you have the source code, API documentation becomes tremendously valuable. Who knows? Maybe you'll even find more than one vulnerability in the code.
Grody Golterson's Hint
Oooo... That's it!
A deal's a deal. Let's talk FPGA.
First, did you know there are people who do this stuff for fun?? I mean, I'm more into picking on other trolls for fun, but whatever. Also, that Prof. Petabyte guy is giving a talk about FPGAs. Weirdo. So hey, good luck or whatever.