11) Customer Complaint Analysis
The terminal challenge for this objective is the terminal "Strace Ltrace Retrace" offered by Tinsel Upatree. Solving this terminal challenge provides additional hints for this objective. To view the hints use the menu on the left.
To start this objective download the jackfrosttower-network.zip available in the objective menu. You will need Wireshark or a network packet reader.
From the hints, we know that Jack Frost Tower sets the evil bit from FRC791 for their communication.
RFC791
To solve this problem, we define a security flag, known as the "evil" bit, in the IPv4 [RFC791] header. Benign packets have this bit set to 0; those that are used for an attack will have the bit set to 1.
The evil bit can be filtered in Wireshark by ip.flags.rb.
Load the provided Jack Frost Tower network capture into Wireshark.
In the filter field type ip.flags.rb != 1. This will filter out all the packets that have the evil bit set. The result shows a HTTP POST request that does not have the evil bit set:
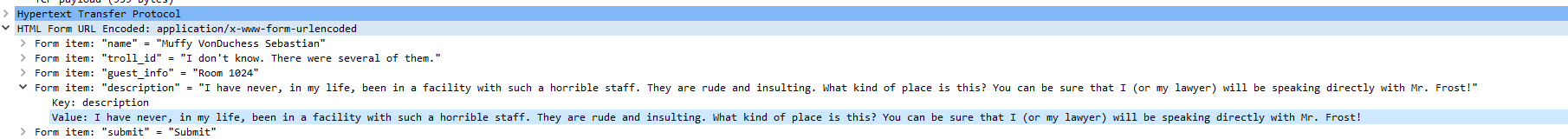
Opening this packet(# 384) shows the following:
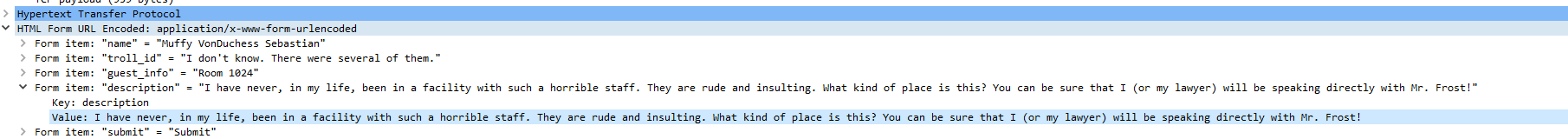
The POST request is a complaint from the Elf Muffy Sebastian VonDuchess in Room 1024.
To search for complaints for room 1024, clear existing filters and add urlencoded-form.value contains "1024". This filter will search for 1024 in the POST request.
The result are 3 packets (384,312, 276):
Packet 384
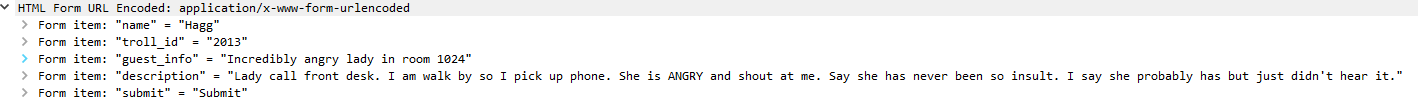
Packet 312
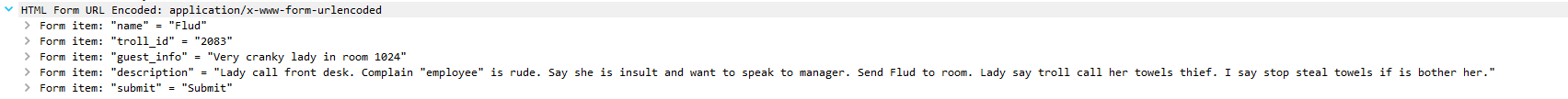
Packet 276
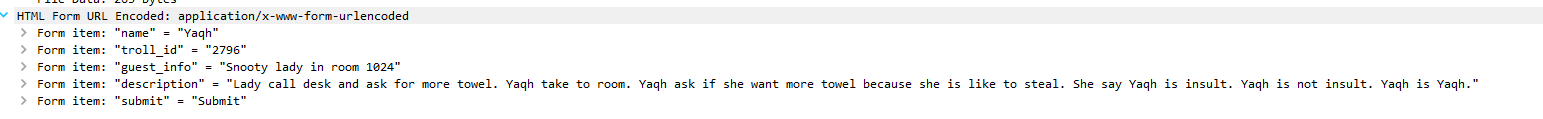
From the above packets you see the three trolls that complained were Flud Hagg Yaqh.
Answer
Flud Hagg Yaqh