Objective 8 - Broken Tag Generator¶
Objective¶
The Tag Generator can be accessed here. The terminal challenge for this objective is Redis Bug Hunt which is offered by Holly Evergreen.
Walk-through¶
Solving the terminal challenge, Redis Bug Hunt, provides additional hints for this objective. To view the hints or the walk-through for this terminal challenge, use the menu on the left.
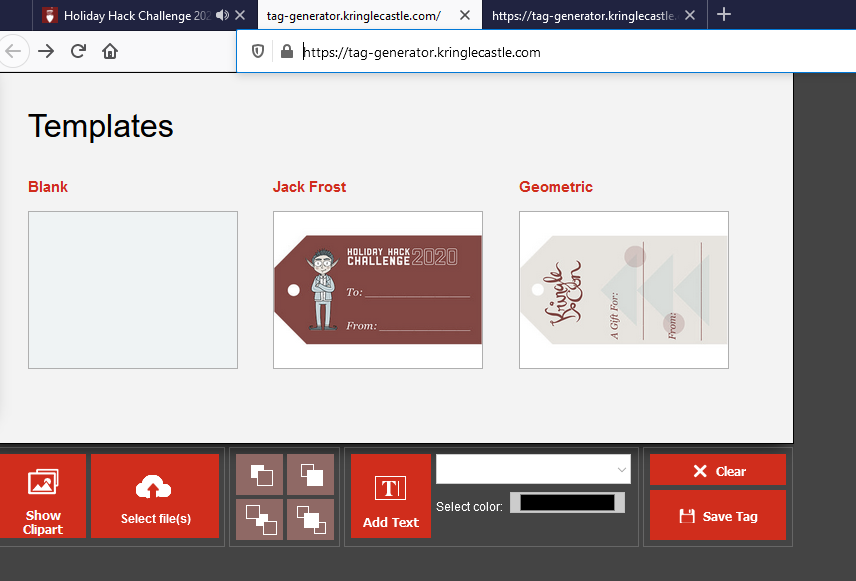
To start this objective go to the Tag Generator website.
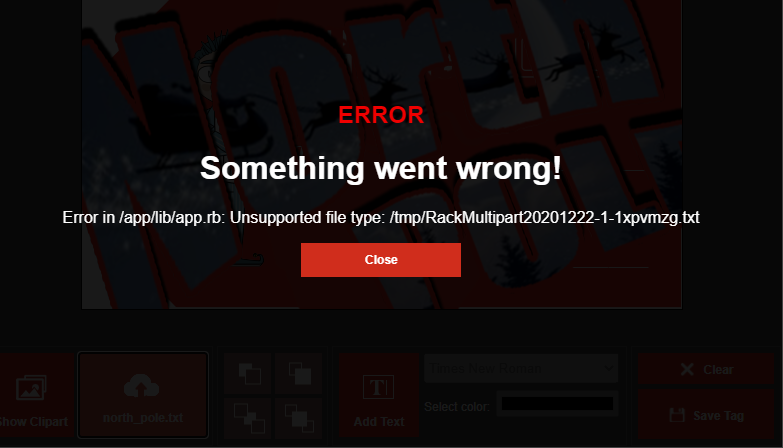
From the hints, you know that the error messages will leak useful information. Click on "Select File(s)" and upload a .txt file.
This tells you the application is located at /app/lib/app.rb.
Upload a valid .png file. Use Chrome Developer mode to identify the location of the uploaded .png file. The uploaded images can be accessed at the following address:
https://tag-generator.kringlecastle.com/image?id=<UID>
Use a path traversal ../../../../app/lib/app.rb to download the app.rb file.
https://tag-generator.kringlecastle.com/image?id=../../../../app/lib/app.rb
The website returns app.rb encoded in Base64.
The path traversal provides the ability to download files from the system. The environment variables for the system can be downloaded with this ability.
Environment variables are located in /etc/environment or /proc/<PID>/environ.
The Tag generator returns a blank response when you try to download /etc/environment. The PID for system process is 1.
Use the following link to read the environment variables on the system.
https://tag-generator.kringlecastle.com/image?id=../../../../proc/1/environ
The above request returns the environment variables encoded in Base64. You can view the results here.
RCE Method¶
You can also solve this objective via Remote Code Execution (RCE). If you review the code, you notice two comment blocks by Jack. These are the blocks that introduce two vulnerabilities. The second block is the vulnerability we used for downloading files through the image endpoint. The first one creates the RCE vulnerability.
# I wonder what this will do? --Jack
# if entry.name !~ /^[a-zA-Z0-9._-]+$/
# raise 'Invalid filename! Filenames may contain letters, numbers, period, underscore, and hyphen'
# end
# Validation is boring! --Jack
# if params['id'] !~ /^[a-zA-Z0-9._-]+$/
# return 400, 'Invalid id! id may contain letters, numbers, period, underscore, and hyphen'
# end
To exploit the RCE, create an image that is larger than 800x600. Give this image the following name ';printevn > printevn2.txt;'.png. Zip this image up and upload it.
Wait a few minutes and then download the results, using the file download vulnerability.
Answer¶
JackFrostWasHere