Objective 6 - Splunk Challenge¶
Objective¶
The Splunk Challenge is offered by Angel Candysalt in the "Great Room". You have to be in Santa's Body to be able to do this challenge. If you're not sure how to enter Santa's Body, refer to Objective 5 write-up.
Walk-through¶
To start this objective go to the "Great Room" as Santa. Refer to Objective 5 walk-through if you're not sure how to enter Santa's Body. Click on the Splunk PC to start this objective. This redirects you to the splunk website for this challenge.
Instead of a hint, this objective contains training questions. The training questions, train users to be able to answer the "Challenge Question".
There is a talk available for this objective.
Training Question 1¶
1) How many distinct MITRE ATT&CK techniques did Alice emulate?
You can find all the attack types following search:
index=T*| top limit=200 index | fields index
Filter the above and remove the duplicates and sub attacks. There are 13 distinct attacks.
Alice Bluebird shares this command with us that also gives the solution:
| tstats count where index=* by index
| search index=T*-win OR T*-main
| rex field=index "(?<technique>t\d+)[\.\-].0*"
| stats dc(technique)
Answer: 13
Training Question 2¶
2) What are the names of the two indexes that contain the results of emulating Enterprise ATT&CK technique 1059.003? (Put them in alphabetical order and separate them with a space)
Search for index=t1059.003*.
Click on the index field in the left toolbar of the results. Two values are displayed, t1059.003-main and t1059.003-win.
Answer: t1059.003-main t1059.003-win
Training Question 3¶
3) One technique that Santa had us simulate deals with 'system information discovery'. What is the full name of the registry key that is queried to determine the MachineGuid?
Alice Bluebird provides the link for Atomic Red Team GitHub repo. Search this repo for "MachineGuid". The registry key is shown in the results.
Answer: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography
Training Question 4¶
4) According to events recorded by the Splunk Attack Range, when was the first OSTAP related atomic test executed? (Please provide the alphanumeric UTC timestamp.)
Search for index=attack field5="ostap*" and look at the earliest attack timestamp in UTC.
Answer: 2020-11-30T17:44:15Z
Training Question 5¶
5) One Atomic Red Team test executed by the Attack Range makes use of an open source package authored by frgnca on GitHub. According to Sysmon (Event Code 1) events in Splunk, what was the ProcessId associated with the first use of this component?
Review the frgnca GitHub repo. The only repo that is related to windows is a repo called AudioDeviceCmdlets.
Search for index=* CommandLine="*audio*" to find the ProcessId.
Answer: 3648
Training Question 6¶
6) Alice ran a simulation of an attacker abusing Windows registry run keys. This technique leveraged a multi-line batch file that was also used by a few other techniques. What is the final command of this multi-line batch file used as part of this simulation?
Search for index=* CommandLine="*.bat*". Add the field CommandLine to the result table. Search and review the .bat files in the results. You will see the following .bat file in the results:
https://raw.githubusercontent.com/redcanaryco/atomic-red-team/master/ARTifacts/Misc/Discovery.bat
Viewing this batch file shows the last line is quser.
Answer: quser
Training Question 7¶
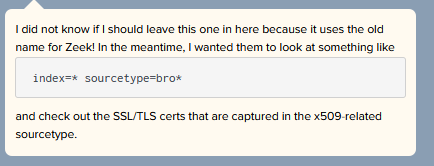
7) According to x509 certificate events captured by Zeek (formerly Bro), what is the serial number of the TLS certificate assigned to the Windows domain controller in the attack range?
For this question we get the following hint:
Search for index=* sourcetype=bro* sourcetype="bro:x509:json". Reviewing the results you find the serial number for win-dc-748.attackrange.local.
Answer: 55FCEEBB21270D9249E86F4B9DC7AA60
Challenge Question¶
7) What is the name of the adversary group that Santa feared would attack KringleCon?
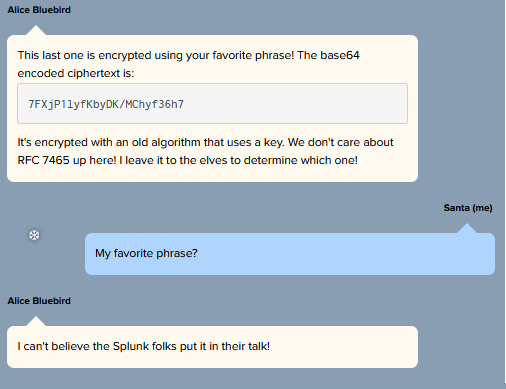
For this question you receive the following message from Alice Bluebird:
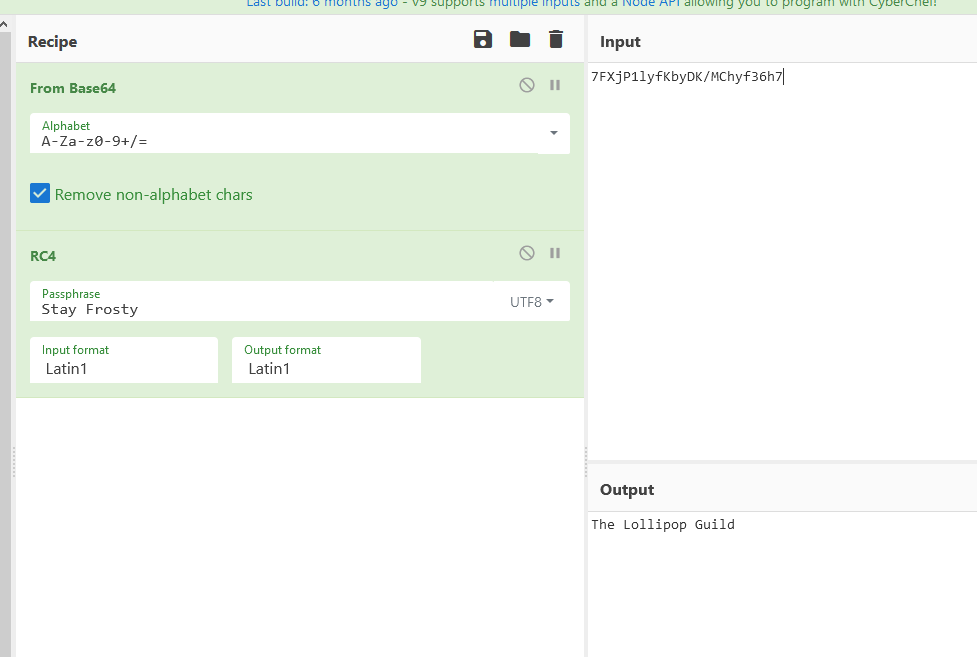
Ciphertext: 7FXjP1lyfKbyDK/MChyf36h7
RFC 7465 refers to RC4. It mentions that the secret code is Santa's favorite phrase. From the Talk for this objective, you know this phrase is "Stay Frosty".
Use CyberChef to decode the adversary group name.
Answer: The Lollipop Guild
Answer¶
The name of the adversary group that Santa feared would attack the KringleCon is The Lollipop Guild.